What is Physical Access Control?
In the United States, property crime accounts for an estimated $15.8 billion in losses, according to the Federal Bureau of Investigation. With this figure likely to grow, enterprise and commercial real estate teams are looking for new ways to protect their buildings and office spaces. Investing in physical access control is a starting point for many of these teams, and with advances in technology, creating a centralized security system has never been easier.
In this blog you will learn:
- The differences between logical and physical access control
- What is physical security?
- How does physical security work?
- The benefits of centralizing video and access control security
The Differences Between Logical and Physical Access Control Systems
IT teams often find themselves tasked with handling multiple aspects of security. Therefore, it’s important to understand the difference between logical and physical access control. A lot of information on the internet conflates the two types, however major differences exist.
What is Logical Access Control?
Logical access control restricts virtual access to computer networks, files, and data (e.g., you type a login password into your computer).
What is Physical Access Control?
Physical access control restricts access to a location. The only way to gain access to a secure area is with the proper credentials such as key cards, fobs and mobile credentials.
Though both types of access control serve unique purposes, they often work in tandem. For example, you might use a logical access control system to secure a computer where your physical access control dashboard is kept. For the purposes of this article, we’ll be focusing solely on physical access control security.
What is Physical Security?
Physical access control is the process of securing an area, like a building, parking garage or office space. A physical access control system (PACS) is often installed to monitor and enforce physical security. PACS prevents unauthorized access to specified areas within a building or its premises.
Often these systems fall into two categories:
- On-premises access control– data servers are housed and maintained on site.
- Cloud-based access control– data servers are housed off-site and maintained by a third-party.
As you’ve probably guessed, on-prem access control systems have been around long before cloud-based systems. They require significantly more maintenance, and the burden of this maintenance falls on the user. For example, if you run on-prem security for an e-commerce enterprise, you better have time and budget reserved for making regular updates and performing maintenance. Updates and integrations for on-premises systems are difficult and take more time to deploy than cloud-based systems. Here are some features of on-premises access control systems:
- Regular maintenance is required.
- Time-consuming provisioning process.
- Difficult to integrate with other security systems.
- Challenging to gain remote access from off-site locations.
Cloud-based access control is helping many IT and security teams centralize their security. G&J Pepsi, JAMF and Shopify are just a few enterprises that Genea has helped implement cloud-based access control in a single pane of glass. Some features of cloud-based access control systems include:
- Servers are housed off-site and maintained by a third party like AWS
- Admins can gain access from anywhere, whether at the office or working remotely
- Easy to integrate with other security and technology systems using API integrations
- Single-pane-of-glass security solution to monitor security globally
One of the major advantages of a cloud-based access control system is its ability to centralize your security. Using API integrations, these access control systems can act as the security hub of your entire tech stack. The cloud easily connects video cameras, motion detectors, elevators, identity management and more. To get started, IT administrators simply enter an API token into the access control platform. Once entered, the system is ready to use.
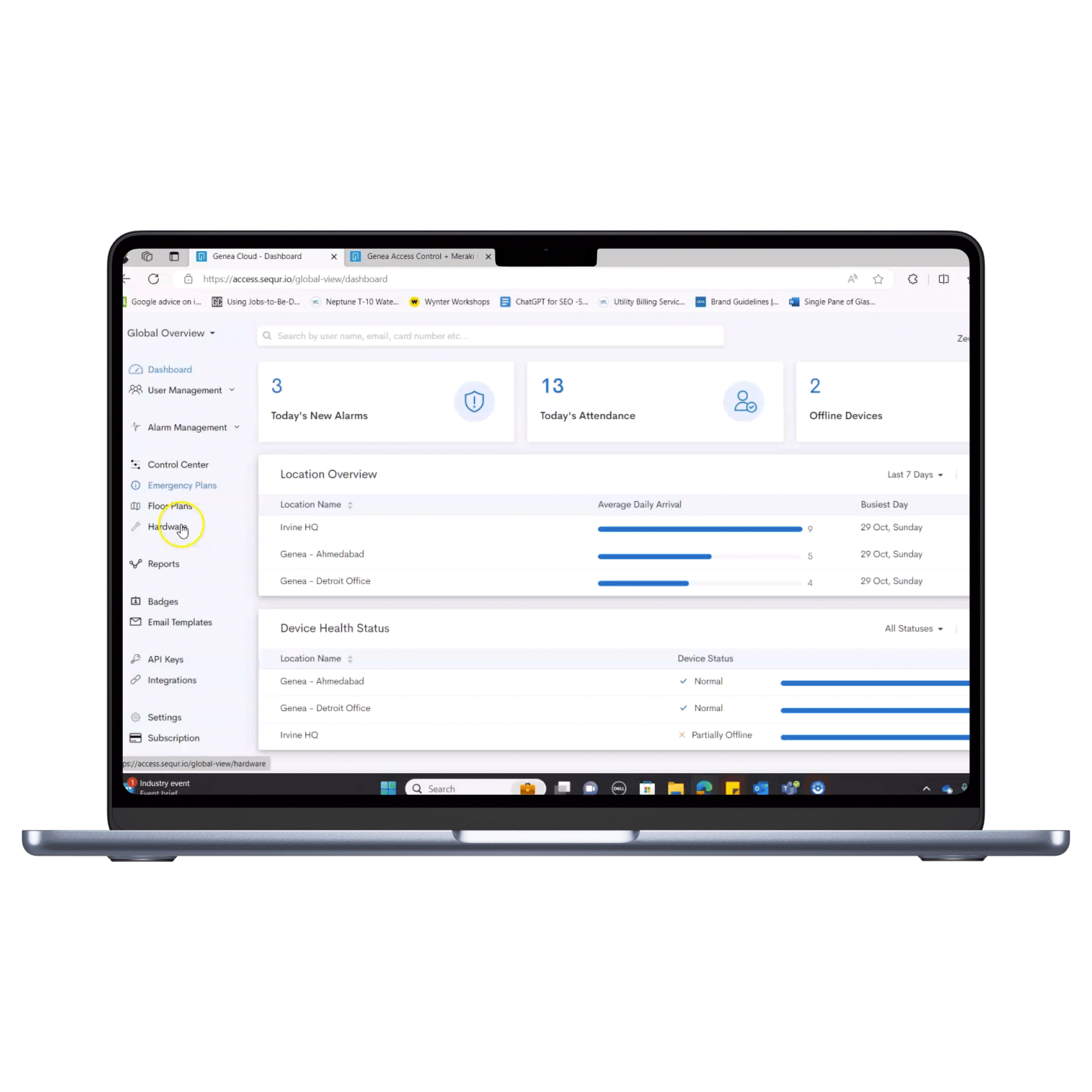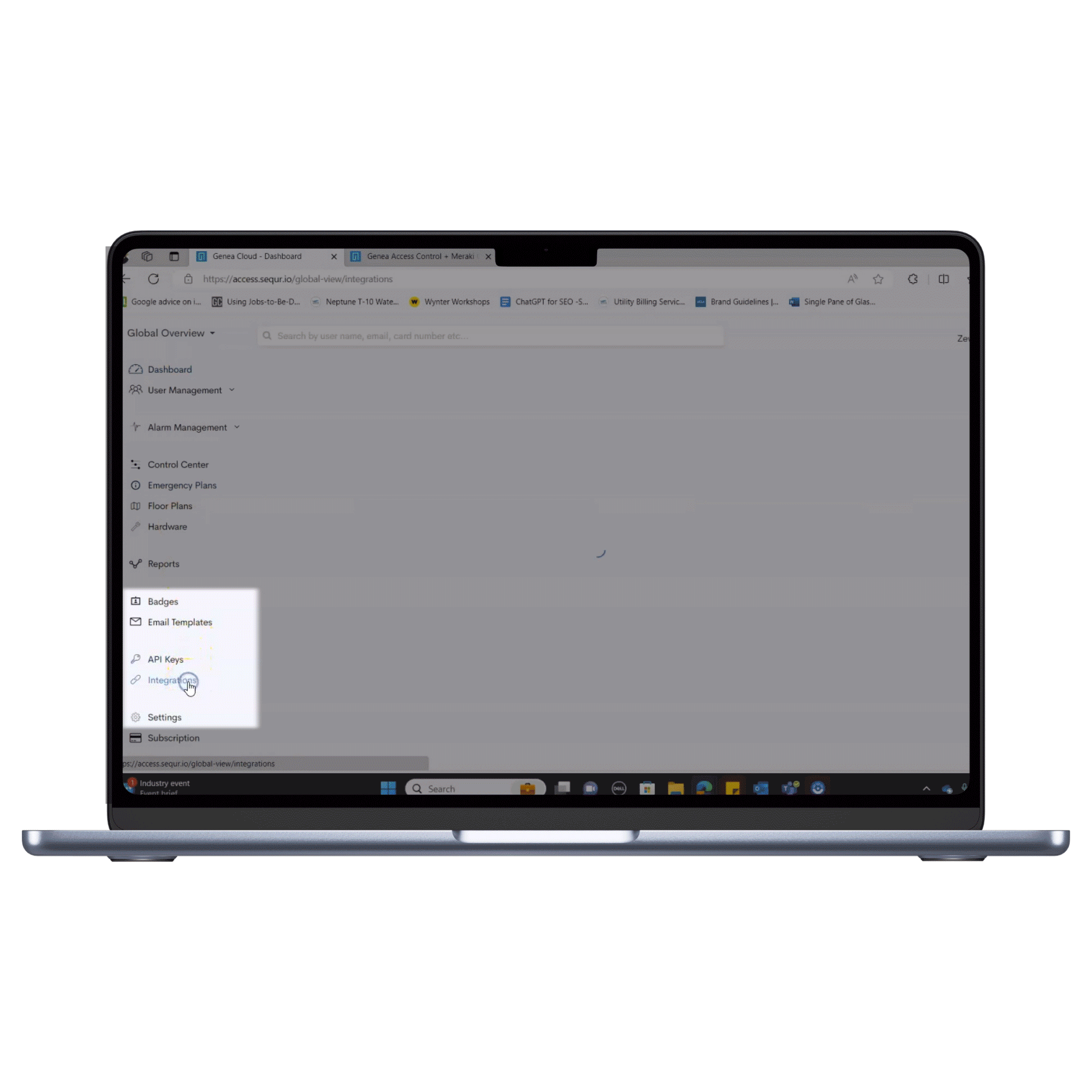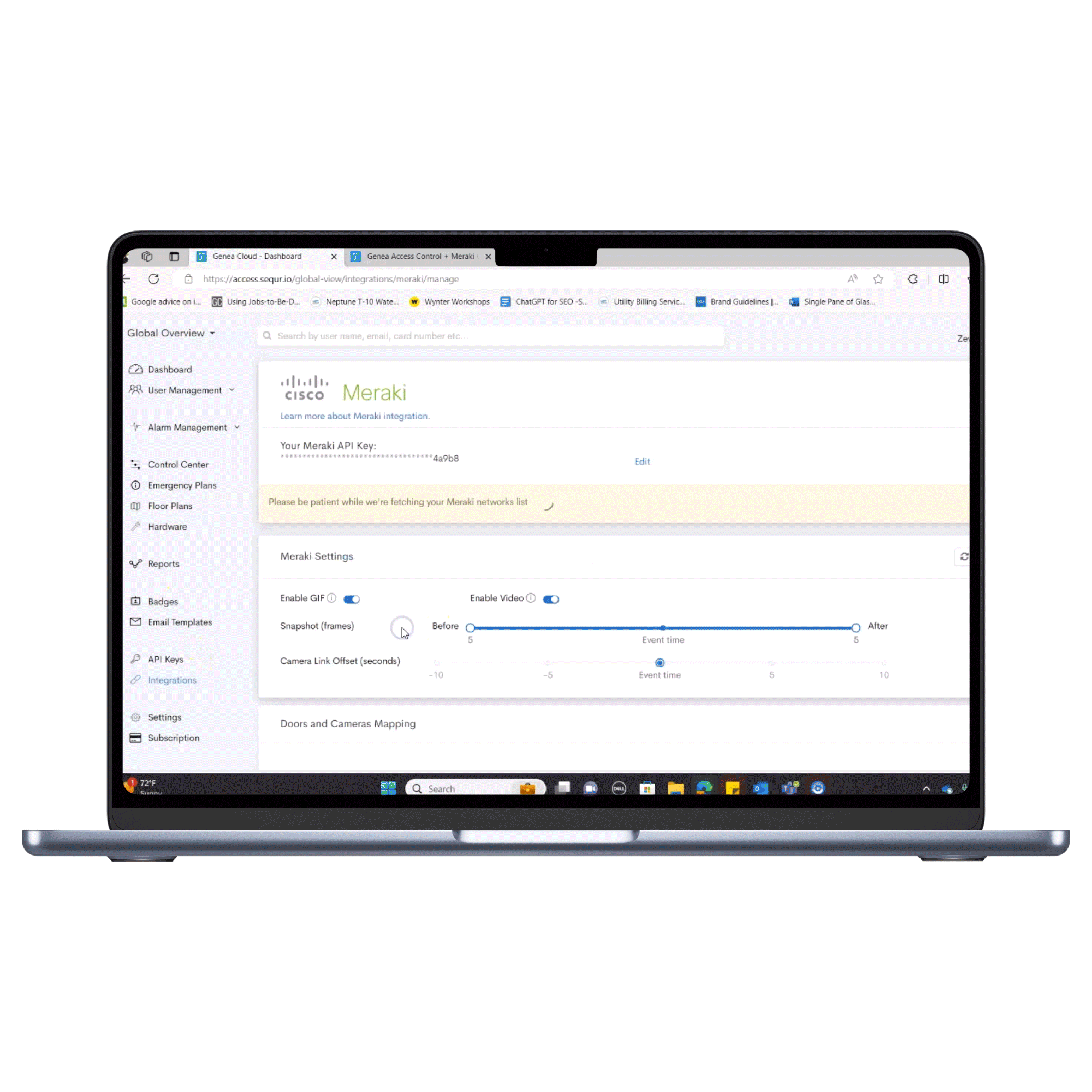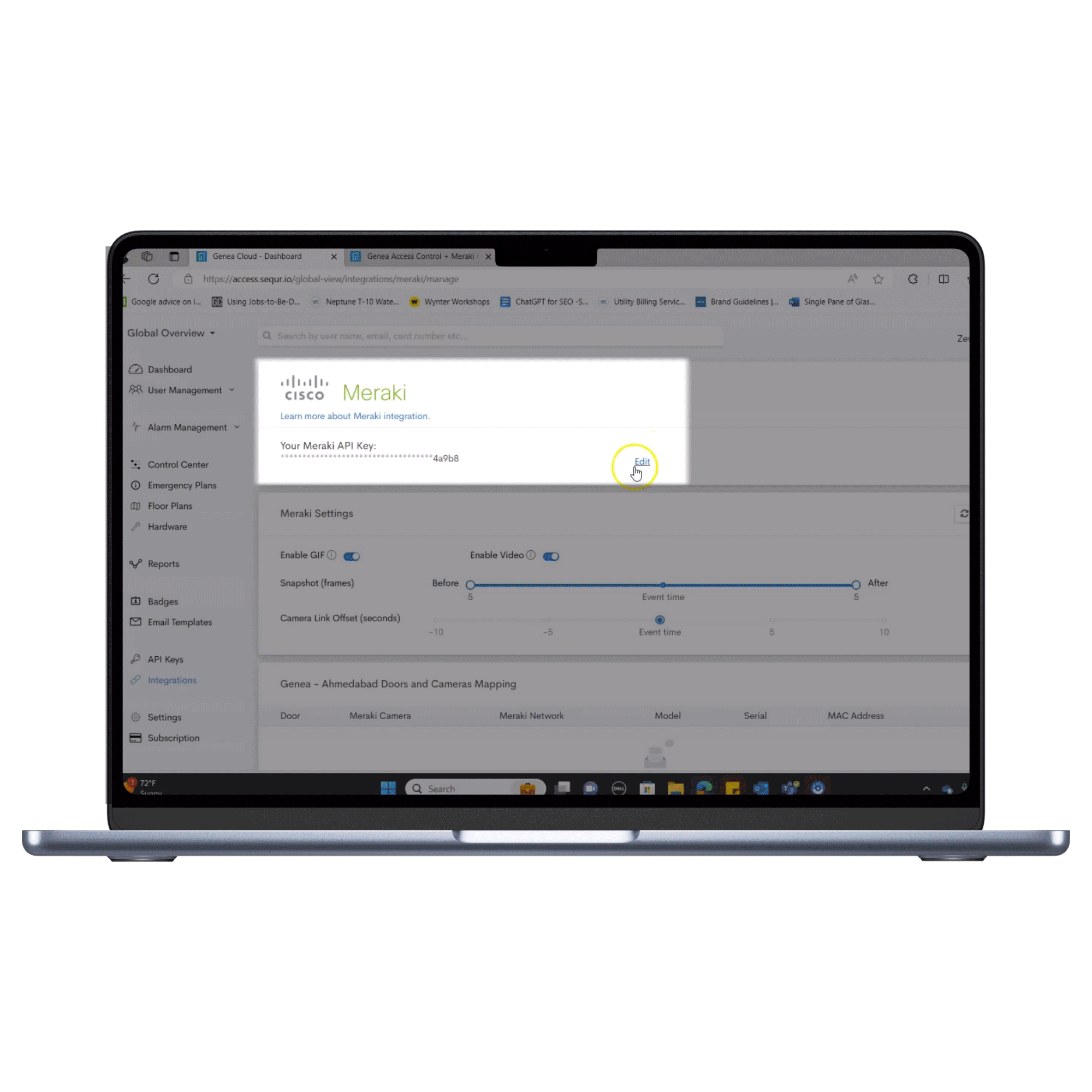
Unlike other cloud security providers, Genea offers many out-of-the-box integrations at no additional cost.
How Does Physical Access Control Work?
Physical access control can be as simple as a lock and key or as complex as a two-factor authentication system. Nowadays, many security teams rely on electronic access control systems built within a single pane of glass. These contain a wide range of components, including user credentials, control panels, wireless door locks, video & visitor management, door reader and access control software. For a complete list of components, check out our blog “How Wireless Access Control Works.”
Basically, these systems function as follows:
- An IT or security administrator grants access privileges to a user (e.g., an employee or visitor).
- The privileges are distributed to the user in the form of a physical credential like a proximity card, key fob or mobile app. Alternatively, Genea customers can access their building or office using an employee badge in Apple Wallet.
- The user shows their credential to a door reader, which, in turn, scans the information.
- The information is transmitted via a network cable to the database where it is verified. From here, the user is let into the area, or if they’re an unauthorized person, the system door will remain locked.
Additionally, as teams develop their security plan, they may choose to combine methods of physical security such as:
- Video Security Systems: found outside and inside commercial and residential buildings. They frequently integrate with logical access control.
- Bollard Fencing and Boom Barriers deter unwanted vehicle traffic. Rising bollards are often cylindrically shaped and planted underground. With restricted access, security teams trigger the bollards to mechanically rise.
- Security Personnel/Human Guards: Catch these guys and gals patrolling parking lots in their security cars or walking the hallways late at night.
- Bulletproof Glass: single-cost, permanent fixture providing immediate defense. These windows are commonly found in banks.
- Mantraps: Mantraps are rooms with two interlocking doors situated across from one another. These are common in banks and high-security areas. A person enters through the first door. When that door shuts, it locks, and the second door unlocks.
Fun Fact
The earliest known locks date back to 4000 B.C. Archeologists discovered these locks at the Palace of Khorsabad in modern-day Iraq. Though crafted from wood, the principle of these prototypical locks remains the same in modern locks. The only alternative to the wooden locks was to post a guard at the site.
Centralized Video Surveillance and Physical Access Control
Video surveillance, also referred to as video management systems (VMS), and cloud-based access control are two critical components of physical security. Traditionally, these on-premises systems could only integrate with other security systems by way of an often expensive, custom-made integration. However, with the advent of cloud-based access control, providers have begun to provide out-of-the-box integrations. In other words, after installation, it’s possible to integrate these systems immediately at no additional charge.
By combining video management with cloud-based access control, administrators create more secure systems, overall. They can watch their doors in real-time and verify access requests using video transmitted to their access control dashboard and reduce the risk of unauthorized entry.
Many VMS’s, like Arcules, Cisco Meraki, and Eagle Eye Systems also offer timelines, camera mapping and camera walls.
How to Strengthen Your Physical Security for the Future
Strengthening your physical security can be as simple as organizing your access control database or as complex as installing a whole new system. Genea’s cloud-based security platform is a user-friendly way to manage your physical assets.
Non-proprietary Hardware
Non-proprietary hardware saves thousands of dollars for companies every year. How? Security providers like Avigilon, Verkada, Kisi and Brivo want to force consumers to be held hostage into their ecosystem. Consequently, if you ever become unhappy with your software provider and decide to change platforms, you’ll have to make costly hardware replacements. Conversely, Genea runs on non-proprietary, Mercury-based hardware, giving you the freedom to change providers at any time. That’s the flexibility you deserve.
Single Pane of Glass for Access Control Security
A major trend in the security industry is a push towards a single-pane-of-glass solution. Instead of toggling through different windows and programs, a single pane of glass lets security teams view various programs from a single window on their computer or smartphone. For example, your video security cameras can be integrated with your access control, visitor management and chat systems. This gives administrators the capability of streamlining their security and responding more quickly to access alerts. The best systems integrate at no additional cost. Here are just a few of Genea’s most popular integrations:
- Video Management Systems- Cisco Meraki, Arcules, Eagle Eye, Milestone & Kite
- Chat Systems- Microsoft Teams, Slack
- Identification Systems- Okta, Azure AD, Google Workspace, SSO
Cloud-based Access Control is the Future
The cloud is quickly overtaking on-premises access control systems. Even traditional security companies like LenelS2, have started investing more heavily in the cloud, but are quickly falling behind. Behind the push for cloud-based systems is the desire to gain access both remotely and on-site. Security teams are finding cloud-based access control gives them both better flexibility and security.
Additionally, cloud-based access control has helped many enterprises, CRE and small- to medium-sized businesses more quickly provision user credentials including mobile keys and badges that can be deployed remotely to users’ smartphones.
Mobile Access Control
With brands like Shopify switching to a digital-first workplace, mobile credentials are becoming more common and something employees’ request. Mobile offers a user-friendly way to eliminate the expense of plastic key cards and provide a seamless access experience. Additionally, mobile helps with security since it is harder to clone and people don’t go anywhere without their phones. When choosing a provider make sure they offer mobile credentialing as well as other physical key card options.
The Bottomline on Physical Security
Whether you choose on-premises or cloud-based access control, the success of your physical security comes down to how you’ve structured your permissions. Delineating which employees get access to which spaces will fortify your security. To do this, administrators should create different levels of security either based on role or user type.
Genea provides many ways to customize your access permissions, so that you can optimize your physical security for the future.
Looking for more information about physical access security? Talk to a Genea representative, today.



