Access control is a confusing product to buy. A ton of industry lingo exists, with an even more convoluted buying process. Beyond those issues, access control is a hard product to install. All of these complexities make a murky mess. Subsequently, customers find themselves locked into terrible software systems with even worse customer service.
Most of this complexity is a smoke-and-mirrors trap, laid by the industry to capture customers. In this post, we’re going to expose one of the most confusing aspects of the access control industry — the open protocol, proprietary system and proprietary hardware dynamic.
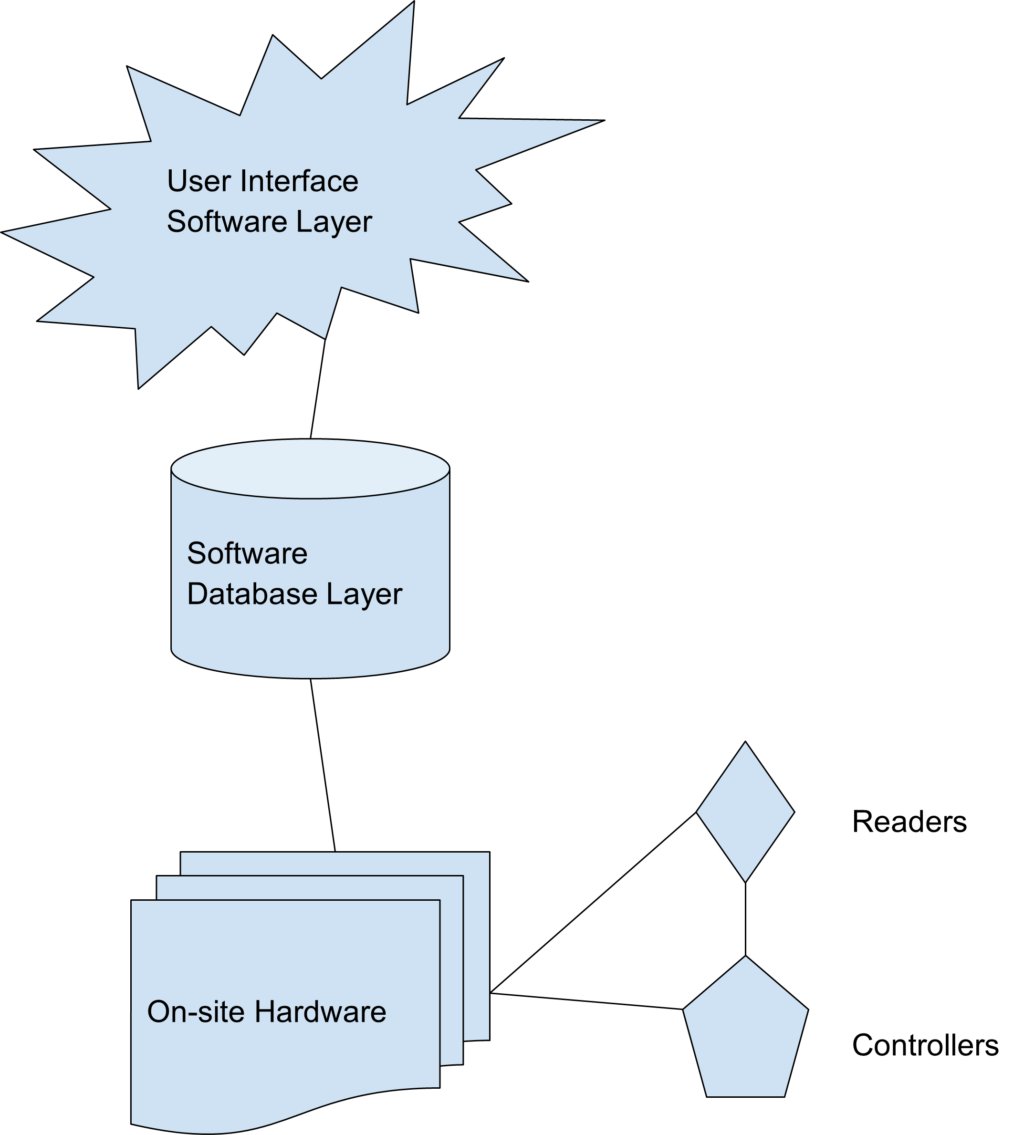
We will define an access control system starting with its software, then transition to its hardware.
What Makes Up an Access Control System?
The following basic components comprise every access control system:
- The software interacts and controls the user data base and on-site hardware. This software can be hosted in the cloud or in an on-premise environment.
- The database contains the users, keys and activity data.
- The hardware consists of the readers and controllers. Most confusion among consumers stems from the hardware. But at their core, all access control systems follow the same basic structure.
Next, let’s dissect the differences and implications of those difference between open hardware systems, proprietary systems and proprietary hardware.
- Open-protocol hardware systems allow any entity with access to the manuhttps://getgenea.com/blog/genea-vs-openpath-for-enterprise-access-control/facturer’s software development kit (SDK) to build new software. Entities with an SDK may control the hardware, too. For example, software products like Genea, Genetec, Avigilon, RS2, Lenel and three dozen others can operate on the same hardware.
- Proprietary system providers create access control that is installed, serviced and supported solely by the manufacturer. These systems come from companies like Kastle and DataWatch.
- A proprietary hardware system contains software and hardware components only functional with one another. These components come from a single source manufacturer. In this case, a third-party system integrator sells, installs and services the system. Third-party integrators familiar with the system provide a less-expensive alternative to service by the manufacturer. The most popular examples of proprietary hardware systems include OpenPath, Brivo, AMAG and Paxton.
Why Understanding Access Control is Important
By understanding these distinctions, customers can make more informed decisions. Additionally, they can protect themselves against predatory vendors. It also protect your future budget. Being locked-in to a completely proprietary system or hardware forces teams to keep barely functioning access control due to the high cost of switching carriers.
If you’re considering an access control system installation or upgrade, make sure to leverage an open protocol hardware system will ensure you retain optionality in the future should you need to change service providers or upgrade systems.
Let us show you the difference of an open access control system complete with an integrated touchless visitor management.



