Arguably the most important benefit of any cloud-based access control system is its feature set. From assigning Custom Roles to viewing enterprise activity in Global Dashboards to monitoring a building with Interactive Floor Plans, cloud-based access control gives users a wide palette of robust features. What’s more, the time it takes to deploy these features is significantly less than with on-premises access control. Which brings us to audit and access logs.
IT and security teams use audit and access logs to better monitor, track and record system changes. In this article, we will unpack the differences between audit logs and access logs, why security professionals use audit logs and how you may benefit from Genea’s Audit Logs for Access Control.
What are Access Logs?
An access log for physical security is a record of entries and exits to a facility or location, such as an office building, enterprise, school or hospital. Access logs typically include information such as the date and time of entry and exit and the name of the person entering or exiting. They are used to monitor and track the movement of people within a facility, ensure compliance with security protocols and investigate security breaches.
What is an Audit Log?
Unlike access logs, which pertain to the physical movement in and out of a facility, audit logs document the digital changes made within a system. For example, when an administrator updates permissions of a user’s credential within the Genea Security platform, the change is documented in an audit log.
Benefits of Audit Logs
Let’s explore the benefits of a detailed audit log feature for physical access control. Audit logs are extremely useful for several reasons. They help enhance security, improve accountability, provide granular information to make better decisions and more.
For example, a national enterprise may rely on security personnel located in different facilities. If an administrator makes a change within the enterprise’s access control platform, the adjustment will be recorded, giving other administrators the opportunity to see what changed and who changed it. Here are some other examples of benefits:
- Enhanced security: Users have the ability to track and monitor all activity in their account, including login attempts, changes to account settings, and any suspicious activity. This helps users identify potential security threats and take action to prevent unauthorized access to their accounts.
- Improved accountability: Audit logs help users keep track of who has accessed their accounts and the changes that have been made. In turn, this improves accountability among team members and prevents mistakes or intentional misuse of user accounts.
- Better decision-making: The information provided by the Audit Log feature can help users make better decisions about how to manage their accounts. By reviewing the activity log, users can identify areas of improvement and take action to optimize their account usage.
- Timesaving: Instead of manually tracking activity in their account, users can rely on the audit logs to automatically record and store all activity. This saves time and reduces the risk of missing important information.
- Troubleshooting: If a problem arises, users can trace the source of the issue and take appropriate action to resolve it.
Audit Logs for Genea Security
Audit Logs for Genea Security is a powerful feature that provides a comprehensive list of all adjustments made on the platform. Admin users can also view a list of all events, filter the results based on specific criteria and export Audit Log data to a CSV file for sharing.
Additionally, system administrators can select a specific user and view a list of user events. This feature can be helpful for monitoring and analyzing the activity of individual users on the platform. Audit Logs displays the actions performed on a specific user and the actions of that user in the Genea platform.
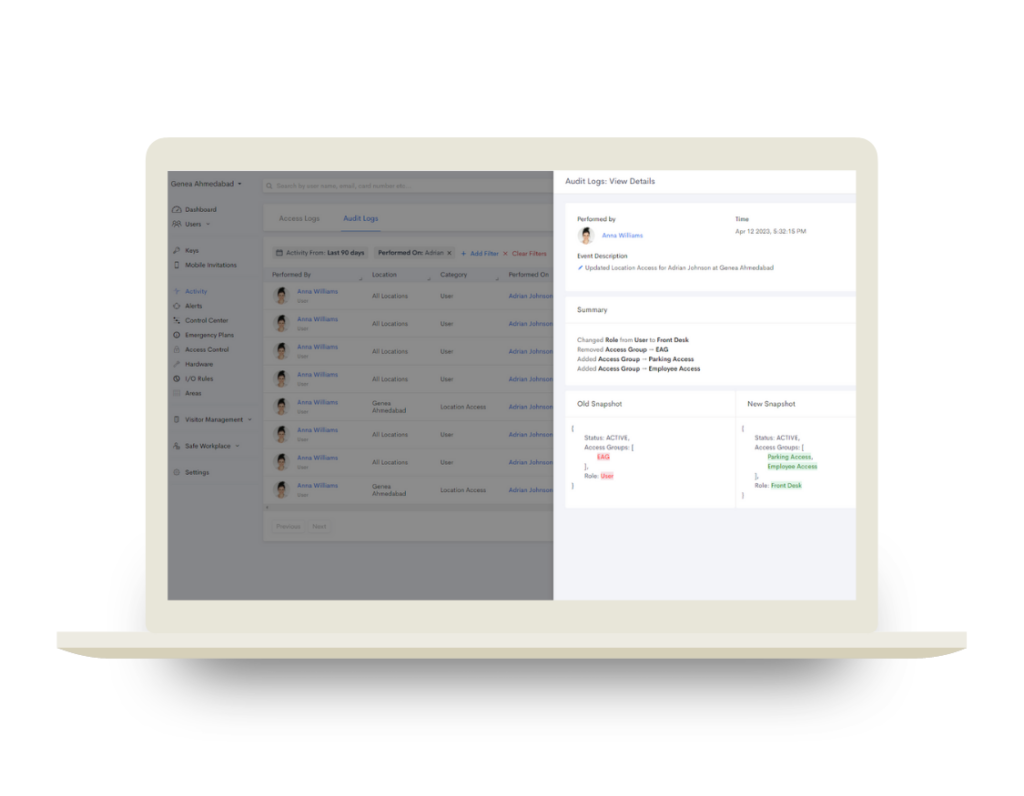
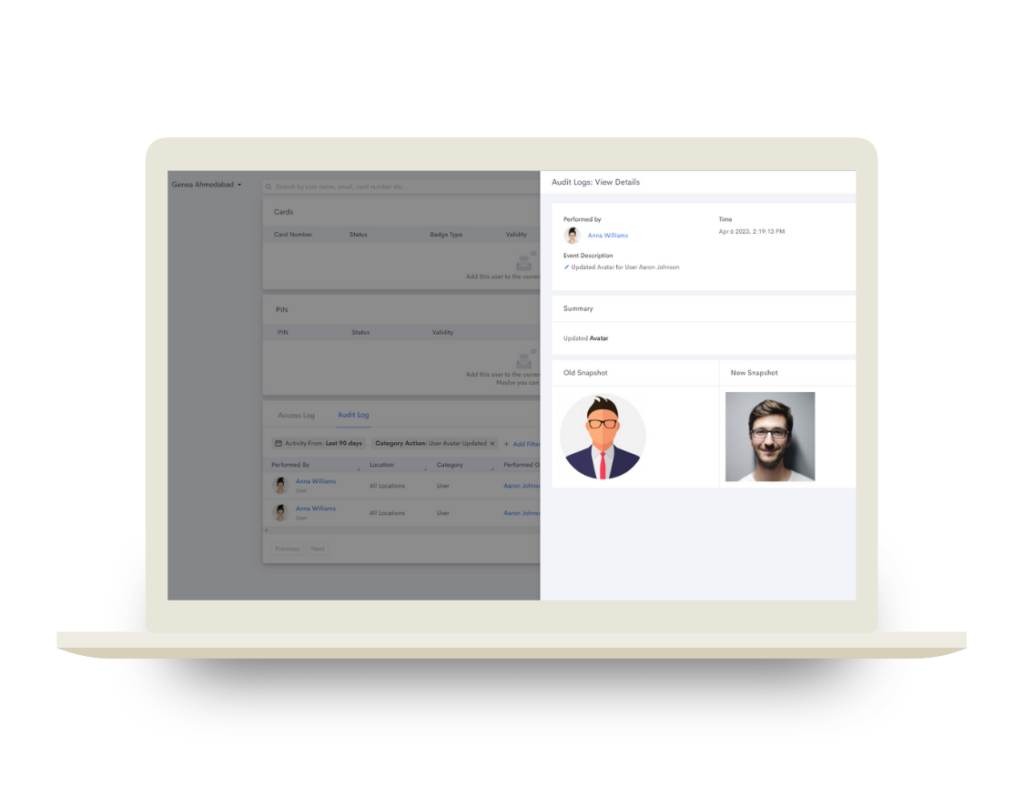
Audit Logs also contains popout windows displaying information about a specific event. The side panel window appears in three sections: Basic, Summary and Snapshot. This feature provides neatly organized data about the actions performed within the Genea platform.
The Basic section shows information about the event, such as who performed it (Performed By), when it occurred (Time) and a description of the event (Event Description). The Summary provides a brief explanation of the event and Snapshot displays the changes that were made during the event.
In summary, the Audit Logs is a powerful feature that can help you monitor activity inside Genea Security. It provides teams with valuable insights and enhanced security.
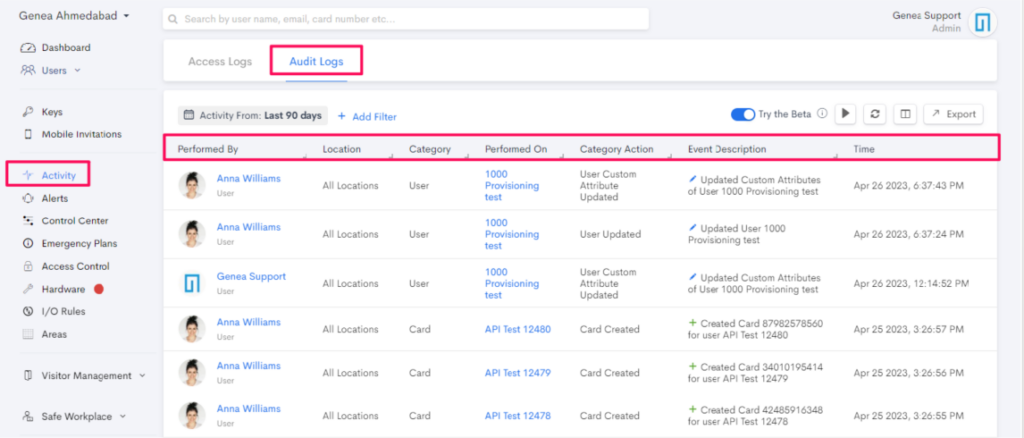
Audit Log Filters
Audit Logs for Genea Security offers various filters to help you narrow down and refine your log view. You can apply multiple filters at a time and clear them all by simply clicking the “Clear Filters” button. Here are the different types of filters available for the Audit Logs:
- Date Filters
- Description
- Location
- Performed By
- Performed By Type
- Performed On
Audit Log Additional Options
Audit Logs for Genea Security provides several options that allow you to customize and manage your log’s appearance. Users can enable or disable live activity recording in the audit log. They can sync the latest activities from the Genea platform.
What are the Benefits of Cloud Access Control?
As mentioned, access logs provide detailed information about the Cloud-based access control has many advantages over its on-premises counterpart. Chiefly among these are:
- API Integrations- A vast array of integrations that come ready to use upon system installation.
- Centralized Security– The ability to connect disparate parts of your physical and logical security. For example, IT and security teams can connect their access control with video management, identity management, and visitor management.
- Scalability– Cloud-based access control helps meet the demands of growing enterprises, hospitals, schools and others, without added server cost.
- Automation- IT and security teams can maximize efficiency in user provisioning (e.g., Employee Badge in Apple Wallet, mobile key cards and physical RFID cards), planning and implementing safety measures and more.
For more information about audit and access control logs, or to learn more about Genea’s cloud-based access control solution, please contact a Genea representative.



